Mission: Cyber Resilience
Our mission is to urgently strengthen the cyber resilience of governments and businesses by facilitating the transfer of critical knowledge and cutting-edge technologies that accelerate the adoption of the Zero Trust Security Model.
By enabling this knowledge and technology transfer, we empower organizations to counter the growing speed, scale, and sophistication of cyber threats – threats that increasingly outpace traditional security capabilities.
Bridging the Knowledge Gap

At HAAP, we enable countries and businesses to stay ahead of rapidly evolving technology, ensuring you don’t fall behind.
In the past, a nation’s progress was measured by the number of engineers it had. But today, that’s no longer enough. The pace of technological change outstrips traditional measures of development, making it essential to continually update skills and expertise.
As the digital landscape evolves, closing the knowledge gap and preventing technological obsolescence is vital. HAAP equips you with the latest tools and knowledge to stay competitive and future-ready.
A Shifting Global Cybersecurity Landscape Requires a Better Approach
In today’s hyper-connected world, where hybrid environments are constantly evolving, traditional cybersecurity strategies are no longer enough.
With decades of experience across a wide range of cybersecurity tools and vendors, we’ve witnessed firsthand how rapidly the threat landscape has changed. Attackers have become more sophisticated, adapting to every new defense we implement.
At this point, deploying top-tier defensive tools is essential—but it’s no longer sufficient on its own. The core principle that must guide cybersecurity today is to trust nothing and always assume a breach.
Even with the most robust defenses in place, vulnerabilities can still be exploited. It’s crucial to be prepared for the inevitable. How you respond when a breach occurs is what truly matters. Zero Trust Segmentation is the solution that ensures breaches remain low-profile and low-impact, protecting your critical systems and data even when attackers gain access

The Dissolving Perimeter

As applications and data centres evolve, attacks are becoming more successful and sophisticated. In the past, organizations managed simple applications in centralized data centres, connecting users and branch offices seamlessly.
However, today’s applications have transformed into complex, multi-tier systems. With the rise of virtual machines, containerized environments like Kubernetes (K8), and microservices architecture, applications now span both on-premises and cloud environments. Remote access—from home or satellite offices—has become the norm.
This shift means the traditional data centre perimeter has dissolved. Security must now adapt to protect data and applications across hybrid environments, where cloud, remote, and on-premises systems intertwine. A new security approach is not just necessary—it’s critical to stay ahead of evolving threats.
The Expanding Attack Surface
The global attack surface has grown exponentially, with breaches now able to originate from anywhere—across cloud environments, remote workstations, and hybrid networks. This shift makes it essential to operate under the assumption that attacks are not a matter of if, but when.
An attacker only needs to succeed once to compromise your system, while your defences must be flawless 100% of the time. This asymmetry is why organizations today must assume they are already breached and take proactive measures to mitigate the impact before it happens.

North-South vs. East-West Traffic: A Paradigm Shift
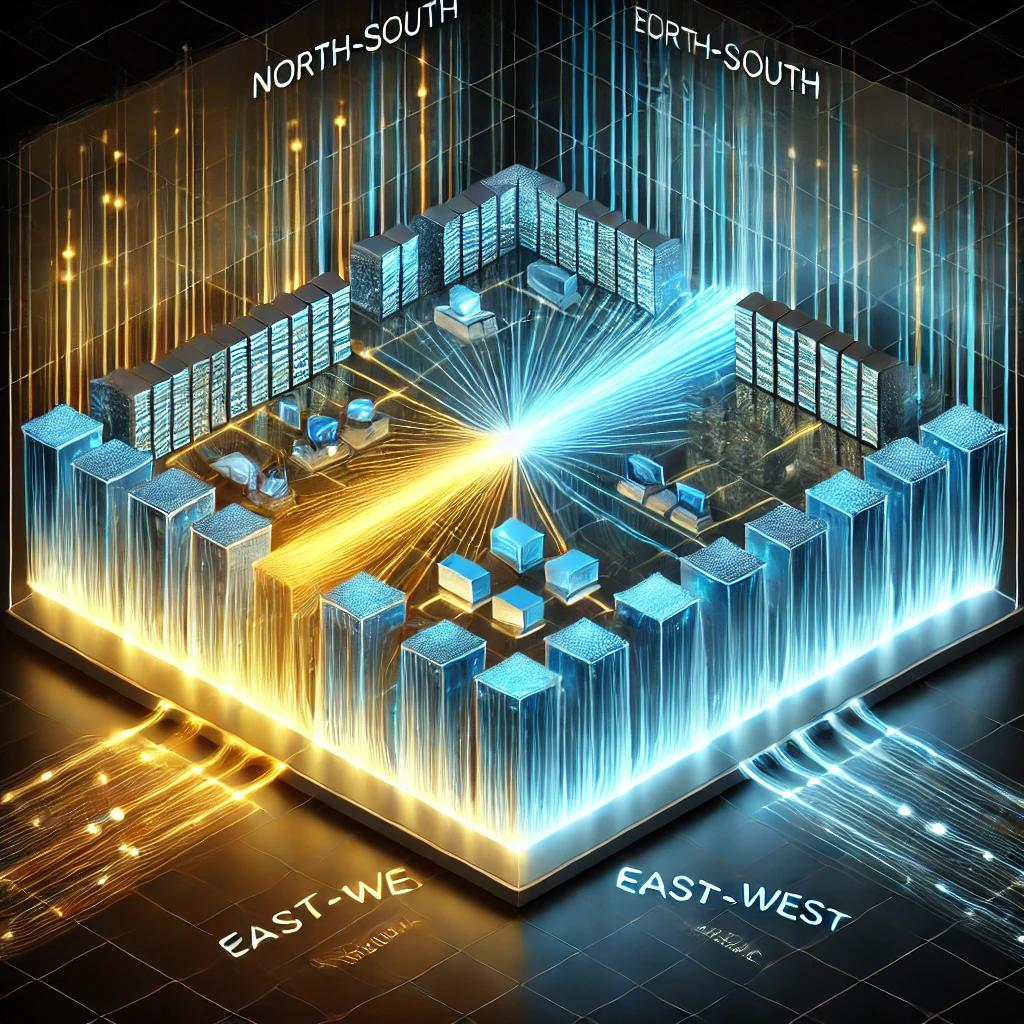
A decade ago, network traffic primarily flowed North-South, moving between data centers and external users. Today, however, the landscape has changed—80% of all traffic now occurs internally (East-West) between applications, services, and devices within the network itself.
This shift means that perimeter defenses alone are no longer sufficient. Companies must prioritize protecting lateral movement within their networks to prevent threats from spreading internally, focusing on comprehensive internal security strategies rather than just securing external access points.
Zero Trust: A Mindset, Not a Product
Zero Trust is more than just a tool—it’s a foundational security philosophy. It rejects the notion of implicit trust, assuming that every access request could be a potential threat. To mitigate these risks, Zero Trust enforces strict, continuous access control policies designed to prevent breaches before they happen.
Unlike traditional security models, Zero Trust isn’t a one-time solution—it’s an ongoing effort that adapts to evolving threats. The process begins by identifying who or what needs access, rigorously verifying each request, and applying security policies at every point of interaction. By adopting a Zero Trust mindset, your security becomes both proactive and dynamic, adapting in real-time to ensure protection at all levels.
Segmentation is the cornerstone of this approach. It extends beyond simple micro-segmentation, diving deeper into finer levels—right down to the workload. This granularity ensures that even if a breach occurs, the damage is contained and controlled, limiting exposure across the system.

Visibility everywhere
Least-priviledge access
Adaptability and consistency
A proactive posture
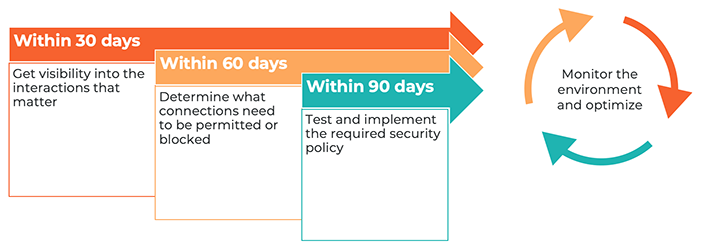
The time for Zero Trust Segmentation is Now

The urgency for Zero Trust Segmentation has never been greater, driven by a growing number of government mandates and regulatory requirements:
- Government mandates: US Executive Order, UK NCSC
- Regulatory requirements: SWIFT, PCI, HIPAA, GDPR
- Cybersecurity frameworks: NIST, ISO 27001, CSF
These regulations require organizations to take a proactive approach to security. Every company must now:
- Understand risk – Classify information assets and identify vulnerabilities.
- Define controls – Implement protective measures that align with identified risks.
- Establish robust processes – Ensure systems are in place to detect and contain security incidents quickly and effectively.
With Zero Trust Segmentation, you can meet these compliance demands while reducing the impact of breaches and ensuring continuous protection in today’s evolving threat landscape.








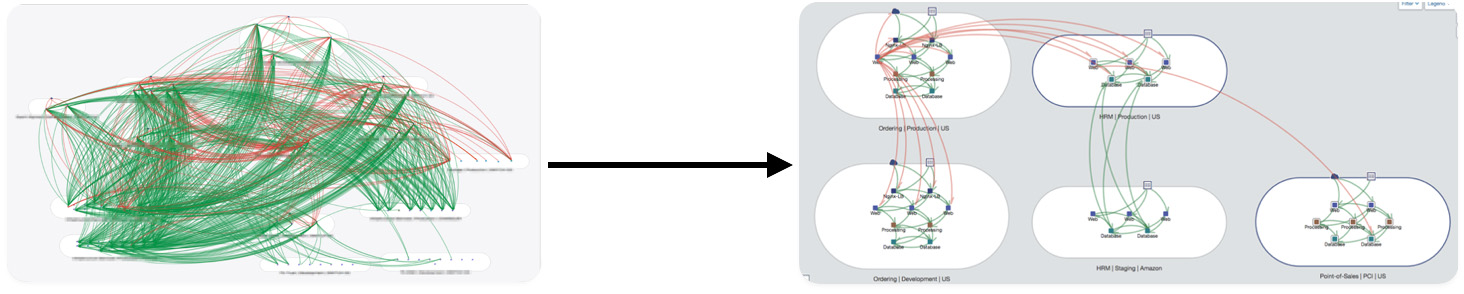
Visibility through workload labelling
Gain complete visibility into your system’s communication flows. With HAAP, move from chaos to clarity, ensuring resilient protection that adapts to today’s ever-evolving threats.
Segmentation: The Core of Zero Trust
Segmentation is the cornerstone of Zero Trust, extending beyond micro-segmentation to even finer levels, down to the workload.
But what is segmentation?Just like a submarine has compartments to avoid sinking in the case of a breach, so your network should be segmented:
Making Segmentation Simple, Fast, and Lightweight
Segmentation doesn’t have to be resource-heavy or complex. Modern approaches are lightweight, leveraging metadata, automation, and machine learning for fast and scalable implementation.
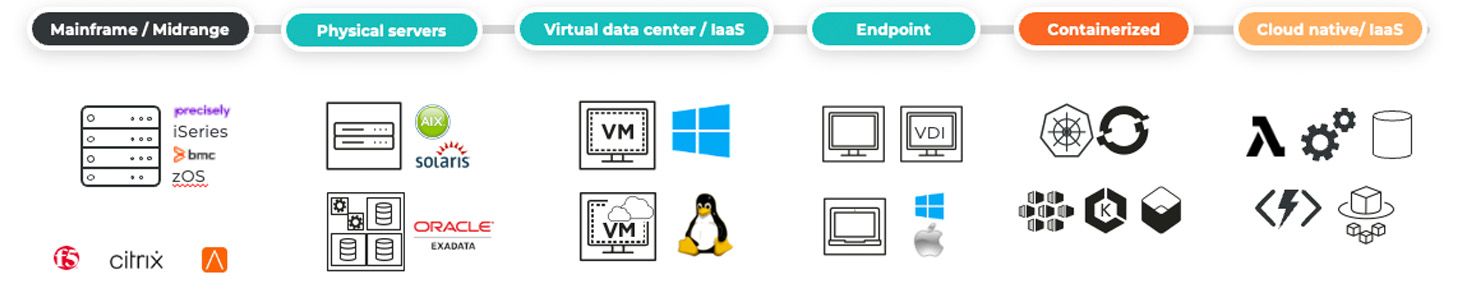
Compatible with most environments
From endpoints and legacy systems to containerized and hybrid cloud environments